In the contemporary digital landscape, fraud has evolved far beyond simple card-theft or forged signatures. Today’s threat actors deploy sophisticated, AI-driven, and automated schemes that easily bypass traditional, rule-based security perimeters. As digital transactions accelerate and the concept of identity becomes increasingly decentralized, organizations must transition from reactive defenses to proactive, intelligence-led strategies.
Modern fraud prevention is no longer a static gatekeeping function; it is a real-time discipline powered by machine learning, behavioral analytics, and strategic data partnerships.
The Shift from Static Rules to Dynamic Intelligence
Historically, fraud detection relied on fixed parameters—such as transaction thresholds, geographic “blacklists,” or shipping address mismatches. While these rules provided a baseline, they are inherently limited and easily manipulated by fraudsters who use automation to probe for vulnerabilities.
To remain resilient, the modern enterprise requires:
- Real-time Decisioning: Analyzing data at the moment of interaction.
- Cross-channel Visibility: Breaking down silos to see the full customer journey.
- Continuous Validation: Moving beyond point-in-time checks to ongoing identity monitoring.
- Predictive Analytics: Identifying intent before a fraudulent act occurs.
Technological Pillars of Modern Defense
1. Advanced Machine Learning & AI
Unlike human analysts, AI models can process millions of data points to identify subtle anomalies.
- Supervised Models refine their accuracy based on known historical fraud cases.
- Unsupervised Models detect emerging, previously unknown patterns.
- Graph Analytics map complex relationships to uncover organized fraud rings and synthetic identity networks.
2. Behavioral Biometrics
Security is shifting from what a user knows (passwords) to how a user behaves. By analyzing typing cadence, mouse movements, and touchscreen pressure, organizations can create a “behavioral fingerprint.” This profile is nearly impossible for bots or human fraudsters to replicate, providing a seamless layer of security.
3. Device Intelligence
Advanced fingerprinting evaluates browser configurations, IP reputation, and device consistency. This is critical for detecting high-risk signals like emulators or bot-driven account takeover (ATO) attempts.
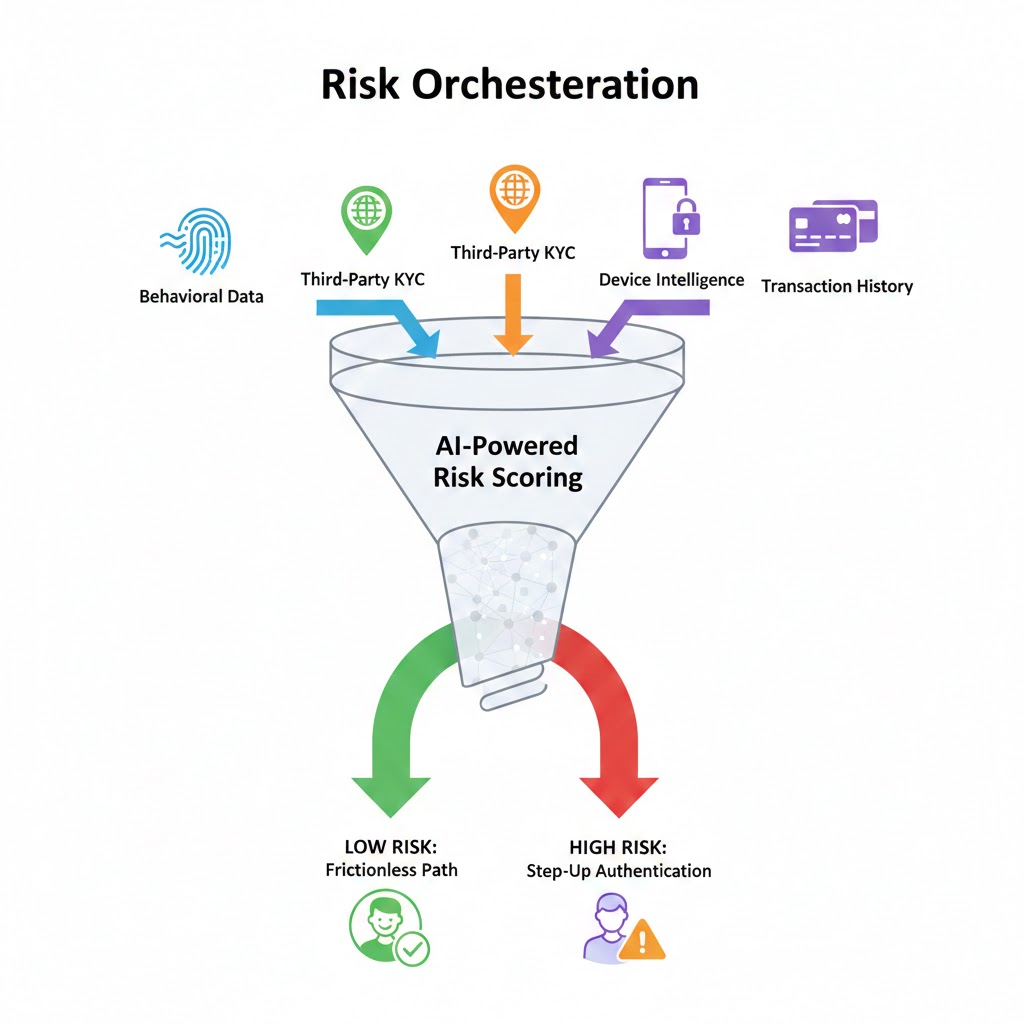
4. Risk Orchestration
The most effective platforms integrate these disparate signals—identity data, transaction velocity, and behavioral scores—into a single orchestration engine. This allows for adaptive authentication, where friction (such as Multi-Factor Authentication) is only applied when the risk score warrants it, preserving the user experience for legitimate customers.
The Critical Role of Third-Party Data
Even the most sophisticated AI is only as effective as the data it processes. Third-party data provides the external context necessary to validate internal signals.
- Identity & KYC Validation: External databases allow for real-time verification of government IDs, sanctions screening, and AML (Anti-Money Laundering) compliance.
- Consortium Intelligence: By participating in data exchanges, organizations can identify known “mule” accounts or compromised devices that have targeted other institutions within the network.
- Digital Reputation: Threat intelligence feeds provide real-time updates on dark web exposures, proxy detections, and botnet activity, extending visibility beyond the organization’s own perimeter.
Navigating Privacy and Ethics
As data usage expands, so does the responsibility to protect it. Organizations must balance innovation with rigorous adherence to global privacy standards such as GDPR and CCPA. Ethical AI—prioritizing transparency in automated decisions and testing for bias in lending models—is essential to maintaining consumer trust. Fraud prevention must be effective, but it must also be fair and explainable.
The Future: AI vs. AI
We have entered an era of “AI vs. AI.” Fraudsters are already using generative AI to create synthetic identities and deepfake documentation. In response, the industry is moving toward a continuous, network-driven model of prevention.
Organizations that successfully integrate high-quality third-party intelligence with advanced analytics will not only reduce fraud losses but also gain a significant competitive advantage. By transforming fraud prevention from a “cost center” into a strategic capability, businesses can protect their reputation while delivering a frictionless experience for their customers.
